Cyber-attacks of various purposes – for warfare or crimes, terrorism or political activism – commonly deploy the same types of cyber-weapons. Typically, (information about) a system vulnerability is embeddCybered into a software code called ‘exploit’ to penetrate the digital system. Additional code, called ‘payload’, is added to cause specific action for a particular target (like putting down an industrial control system, or sniffing and exfiltrating sensitive data). Unlike in the physical space, vulnerabilities can be discovered (and exploits and payloads developed) by civilians and groups that possess particular knowledge, rather than vast (financial and human) resources, such as companies or states. Vulnerabilities discovered in various available software or hardware should be responsibly disclosed to the authors, in order to issue patches and secure the services provided. This, however, is not a common scenario. Instead, vulnerabilities are traded and developed into weapons by various parties – including governments; and ignored by many – including companies and end-users. The responsibility for global cyber(in)security is, therefore, shared.
You may also be interested in

Digital Commerce Course: a five-year assessment
The publication evaluates the impact of the Digital Commerce Course, aimed at providing capacity building on e-commerce to trade professionals. Over the years, the course has helped trade negotiators navigate an ever more complex e-commerce agenda, which currently encompasses a vast range of issues, from trade facilitation to data protection and cross-border data flows. This course has been offered for five years (2017-2021) by means of a partnership between Diplo Foundation, CUTS International Geneva, the International Trade Centre and the Geneva Internet Platform. For more information about ...

Local hubs and the work of the RPWG
'It was also very important for me to join other members of the RPWG to be physically present at the IGF, so we could follow the implementation of the RP mechanism, working in partnership with the Secretariat... and providing assistance to the hubs.' - Marilia Maciel from Brazil

Rapport: Des voix africaines plus fortes dans le numérique : construire une politique étrangère et une diplomatie africaines du numérique
À mesure que le dynamisme numérique de l'Afrique s'accroît, sa participation à la politique numérique mondiale doit augmenter. Dans cette transition, les pays africains doivent composer avec les réalités géopolitiques de notre époque.

The Role of Regional Cooperation in Eradicating Poverty and Aid Dependency in East Africa
The hypothesis of this thesis is that regional cooperation and integration are effective tools in alleviating poverty within nations and reducing their dependency on foreign or development aid.

Connecting Asia and Europe | ASEF Outlook Report 2016/2017 | Volume I: Data on Connectivity
The ASEF Outlook Report 2016/2017 Volume I delves into data on various dimensions of Asia-Europe connectivity including digital, economics, sustainable development, culture, media, education, and governance.

Dealing with cybersecurity challenges
'Various governments have come up with different interventions to address these challenges, like cybersecurity which is on the rise. The development of human resource and capacity building has been identified as one of the stumbling blocks.' - Godfrey Ahuma from Ghana
Report of the Working Group on Internet Governance
The Working Group on Internet Governance discusses the need for international cooperation to address challenges in internet governance. They emphasize the importance of multistakeholder participation, human rights protection, and transparency in decision-making processes. The report outlines principles for effective governance, such as inclusivity, accountability, and sustainability. The Working Group calls for ongoing dialogue and collaboration among governments, private sector entities, civil society organizations, and technical communities to ensure a secure and open internet for all.

E-teaching social programmes
'I had to use all possible means of getting people to participate actively in the programme... What learning style does a person have? Is it part of his or her culture or not? These were the questions for which I looked to find answers.' - Veronica Cretu from Moldova
New threats: the cyber-dimension
The text discusses emerging cyber threats and the need for increased cybersecurity measures to address these new challenges.

Cybersecurity in the Western Balkans: Policy gaps and cooperation opportunities
Report on cybersecurity cooperation in the Western Balkans.

Introducing child safety in Romanian schools: Does the existing primary and secondary curriculum address online safety?
This paper examines the idea of an online child safety policy for Romania, which would provide an initiative to encourage smart online behavior in young children, prepare them to surf the Internet, and educate them to avoid its dangers. As technology develops and more and more children spend time online, they are exposed to numerous threats, dangers and potential abuse. Children need to learn how to behave online, how to critically assess their activities online and act accordingly.

AI Apprenticeship: Learning about AI by developing AI
AI Apprenticeship publication explores how learning by building can equip professionals with the skills, ethics, and adaptability needed for the AI era. Inspired by the Swiss vocational model, it presents a human-centred approach to navigating digital transformation. Drawing on DiploFoundation’s experience, it demonstrates how even non-technical professionals can gain confidence and competence in using AI.

Climate Change and Human Rights: A Rough Guide
This text provides an overview of the intersection between climate change and human rights, emphasizing the impacts on vulnerable populations and the need to address these issues to protect human rights.

Cloud computing: Opportunities and issues for developing countries
This paper looks at how cloud computing will surpass the Internet in adoption and usage as this technology’s users are on the other side of the digital divide. It looks at the diffusion of mobile phones and devices in developing countries and its continuous dramatic rise and at some popular mobile applications that are helping development efforts, such as m-Banking, m-Education, m-Health, m-Agriculture, and others that already exist and are popular within developing countries.

Stronger digital voices from Africa: Building African digital foreign policy and diplomacy
As Africa’s digital dynamism grows, its participation in global digital policy must increase. In this
transition, African countries have to navigate the geopolitical realities of our times.
The report is also available in French.

Development Co-operation Report 2014: Mobilising Resources for Sustainable Development
The Development Co-operation Report 2014 emphasizes the importance of mobilizing resources for sustainable development. It highlights the need for effective partnerships, innovative financing mechanisms, and increased transparency to achieve development goals. The report also stresses the importance of policy coherence, human rights-based approaches, and the engagement of a wide range of stakeholders in development efforts.
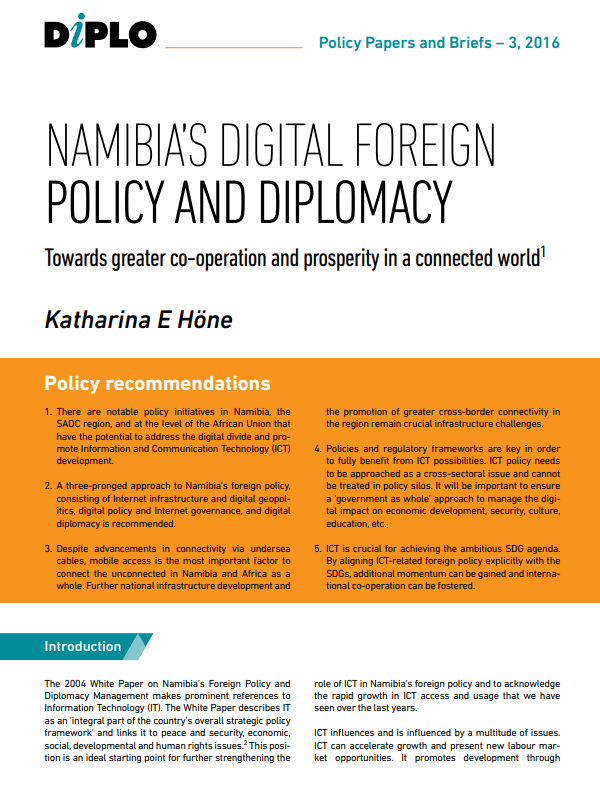
Namibia’s Digital Foreign Policy and Diplomacy (Briefing Paper #3)
This briefing paper emerged from Diplo's participation in Namibia's Foreign Policy Review Conference (July 2016). In this paper, Dr Katharina E. Höne suggests a three-pronged approach to Namibia's digital foreign policy and diplomacy, and looks at the discourse on information and communications technology (ICT) and development.

Coming soon: Internet Governance: Issues, Actors and Divides | 8th Edition
The forthcoming 8th edition of Internet Governance: Issues, Actors and Divides by Jovan Kurbalija marks a major milestone in the ongoing effort to understand and shape the global digital landscape. First published nearly two decades ago, this seminal work returns in 2025 with fresh insights, responding to the urgent need for clarity and action in today’s dynamic digital policy environment.

Teaching computer literacy to alleviate poverty
'I am involved in strengthening education policies at a global level through a forum that will bring representatives from national and international organizations, experts, teachers, NGOs and the youth who are engaged in education...' - Charity Gamboa from the Philippines

Global Public Goods: International Cooperation in the 21st Century
This collection of papers offers a new rationale and framework for international development cooperation. Its main argument is that in actual practice development cooperation has already moved beyond aid. In the name of aid (i.e., assistance to poor countries), we are today dealing with issues such as the ozone hole, global climate change, HIV, drug trafficking, and financial volatility. All of these issues are not really poverty related. Rather, they concern global housekeeping: ensuring an adequate provision of global public goods. Many important lessons could be drawn by first recognizing t...

Lethal Autonomous Weapons Systems: Mapping the GGE Debate (Briefing Paper #8)
The paper discusses the ongoing debate in the Group of Governmental Experts (GGE) on Lethal Autonomous Weapons Systems (LAWS) and the varying perspectives on the need for regulation and control of these weapons.

Cybersecurity in the Republic of Fiji
This paper discusses cybersecurity in Fiji and offers recommendations to challenges such as the vulnerability of systems due to lack of a cybersecurity framework. The poorly framed laws and lack of appropriate policies.
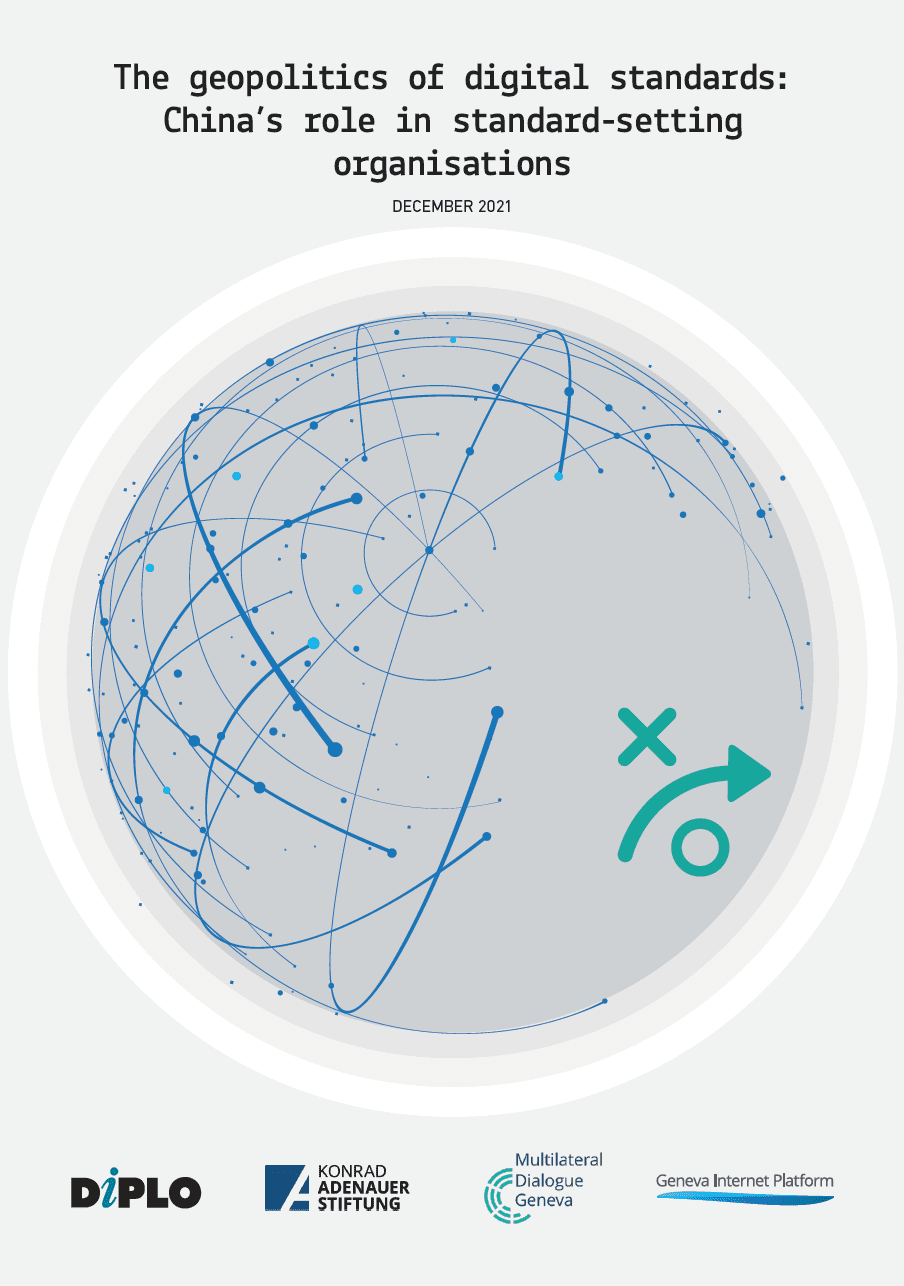
The geopolitics of digital standards: China’s role in standard-setting organisations
Standards for digital technologies are all around us, enabling devices to interact with each other, allowing us to connect to mobile networks, and facilitating the exchange of information. By providing rules or guidelines for the development and functioning of technologies, products, and services, standards foster interoperability and enable safety and quality of service. This report provides an overview of the digital standardisation ecosystem and explores China’s role within this ecosystem.

Tunis Agenda for the Information Society
The Tunis Agenda for the Information Society highlights the need to bridge the digital divide, prioritize the development of ICT infrastructure in developing countries, promote internet governance principles, and ensure a people-centered, inclusive, and development-oriented information society. It emphasizes the importance of multilateralism, capacity building, and creating an enabling environment for sustainable ICT development. The document serves as a roadmap for advancing the global information society and ha...
Mediation and artificial intelligence: Notes on the future of international conflict resolution
Over the last years AI has emerged as a hot topic with regard to its impact on our political, social, and economic lives.

Net neutrality in Europe
The European Union upholds net neutrality, ensuring that all internet traffic is treated equally, without discrimination or interference from internet service providers. This regulation protects consumers' rights to access online content freely and without limitations set by providers.

Inclusive Internet Governance
In this paper, Derrick Cogburn outlines a vision for multistakeholder democratic participation in global information and communication policy processes. Drawing on international regime theory, Cogburn suggests that the UN World Summit on the Information Society (WSIS) is an explicit attempt to formulate the principles, norms, and values of an emergent international regime to govern the information society in general, and the Internet specifically.

Common African Position on the Post-2015 Development Agenda
The participatory approach that led to the elaboration of the Common African Position (CAP) on the post-2015 Development Agenda involving stakeholders at the national, regional and continental levels among the public and private sectors, parliamentarians, civil society organizations (CSOs), including women and youth associations, and academia. This approach has helped address the consultation gap in the initial preparation and formulation of the Millennium Development Goals (MDGs).

Global Inviolability of the Internet Root Zone (Briefing Paper #1)
Dr Kurbalija explains the internet root zone, and highlights the context and controversy of questions about its inviolability. Possible solutions identified by him include legal elements (customary law, diplomatic law, common heritage of mankind), 'software' inviolability, and 'hardware' inviolability.

The road to dignity by 2030: ending poverty, transforming all lives and protecting the planet
The message emphasizes the goal of achieving dignity by 2030 through ending poverty, transforming lives, and preserving the environment.
IGCBP2011 research project summaries for EuroDIG 2011
The publication contains research project summaries written by students of the 2011 Research Phase of the Internet Governance Capacity Building Programme (IGCBP2011). The summaries were presented during EuroDIG 2011.

Adoption and adaptation of e-health systems for developing nations: The case of Botswana (Research by Benson Ncube)
This paper seeks appropriate solutions to improve the access and capability of the health delivery systems in Botswana. The research reveals that many countries are now using information-based services to assist in the administration and delivery of medical services via telecommunication infrastructures.

Empowering women in the IG process
'At the ICANN meeting in Puerto Rico last year I was not aware of anything unusual in the demographics, but in Hyderabad I noticed that while men of my age were quite well-represented, there were comparatively few women...' - Deirdre Williams from St Lucia

Developing Community-level Capacity Assessment Tools: Perspectives and Practical Applications in the Context of Rural Africa (Briefing Paper #11)
The message provides an overview of developing community-level capacity assessment tools relevant to rural Africa to improve local development strategies.

Diplomacy as an instrument of good governance
The functioning of diplomacy is influenced by a complicated combination of different interrelated factors. This paper briefly analyses their impact on the evolution of diplomacy and discusses how diplomacy as an instrument of good governance should adjust itself to meet the new challenges, to become more relevant, open and agile, to modify its methods and to fully utilise opportunities offered by the technological revolution.

Une introduction à la gouvernance d’Internet
La gouvernance d’Internet n’est pas un sujet simple. Bien qu’elle traite d’une notion qui se veut être un symbole représentatif majeur du monde numérique, elle ne peut pas être abordée avec une simple logique numérique binaire qui ne reconnait que le vrai et le faux, le bon et le mauvais.

Addressing the Digital Divide in the Joint Statement Initiative on E-Commerce: from enabling issues to data and source code provisions
This paper examines the evolution of the ‘digital divide’, especially in the context of the WTO Joint Statement Initiative on Electronic Commerce. As an integral part of its analysis, the paper examines textual proposals raised under the current Joint Statement Initiative (JSI) negotiations, especially those submissions on data flows, data localization, and source code. This study has been produced under a project implemented by the International Institute for Sustainable Development (IISD), in consortium with CUTS International, Geneva; BKP Economic Advisors; and InterAnalysis. It was pub...

A study of the UN Working Group on IG – MSP in communication technology for development at the global level
The paper aims to identify best practices and lessons learned in multi-stakeholder partnership (MSP) practices at the global policy level through a participatory methodology based on interviews and an online electronic survey.

Maturity of cybersecurity initiatives in Malawi: A comparison with the drive for fast and ubiquitous Internet connectivity
This study looks at the current state of cybersecurity initiatives in Malawi against a background of significant efforts to greatly enhance Internet connectivity speeds and access. Focus is therefore placed on cybersecurity-related standards, policies and legislation, and cybercrime law, as well as higher- and end-user-education programmes.

Re-imagining the future
‘There is so much work still to be done. There are so many unraveling threads. There is so much still to create. There is much need to better use the Internet for development.’ - Sheba Mohammid from Trinidad and Tobago

In search of the most sustainable and coherent diplomatic approaches to addressing the fundamental challenges Small States (including Small Island States or SIDS) perennially face in an uncertain world of hegemonic giants
Small states, in every sphere of natural and human activity, are negatively and disproportionately impacted by crises, when compared to their hegemonic, larger and stronger counterparts.

Developing ICT for youth and people in rural settings
'There is a huge need for online learning infrastructure at the national level in my country and I am sure it is the same in other small island developing states... I encourage governments to have their public servants, in particular youth to study Internet governance...' - Fuatai Purcell from Samoa

Freedom on the Net 2015
The Freedom on the Net 2015 report assesses global internet freedom, highlighting increasing government censorship and surveillance. Internet freedom is in decline due to various restrictive measures taken by governments, impacting users' rights and privacy. The report warns that the situation could worsen if unchecked, emphasizing the importance of protecting freedom of expression and online rights. Despite challenges, it also notes positive developments, such as the use of social media for activism and the expansion of internet access.

Incorporating IG issues into teaching
‘I strongly believe that personal development is most important for my teaching and research. Indeed, I have always been keen to improve my areas of expertise and share newly acquired knowledge with my students.’ - Lenandlar Singh from Guyana

ICANN and internet governance: sorting through the debris of ‘self-regulation’
This message explores the challenges and complexities of internet governance, highlighting the need to navigate the aftermath of relying on 'self-regulation' within ICANN.

Improving the practice of cyber diplomacy: Training, tools, and other resources – Final study
This study analyses the capacity development of cyber diplomacy, including training opportunities, tools, and other resources, and looks at their reach, take-up, and what should come next. Why? Because although cyber diplomacy, the conduct of diplomacy with respect to a state’s interests in cyberspace, is too important to ignore, the participation of countries is far from ideal.

Digital Commerce Capacity Development
This publication presents the thematic approach, methodology, achievements and lessons learned from a capacity development initiative on e-commerce jointly offered in 2017/2018 by DiploFoundation, CUTS International Geneva, the International Trade Centre (ITC), the Geneva Internet Platform(GIP), and delivered with the United Nations Conference on Trade and Development (UNCTAD).

Development diplomacy and poverty reduction strategy
Lichia Yiu and Raymond Sanner describe in detail the application of development diplomacy in the context of international co-operation for poverty reduction in Highly Indebted Poor Countries. In particular, the authors describe the goal of the International Labour Organisation – a non-state actor – in advocating the inclusion of employment and Decent Work Agenda policies in Poverty Reduction Strategy Papers, an instrument developed by the International Monetary Fund and the World Bank.
Reframing Internet Governance Discourse: Fifteen Baseline Propositions
The text presents fifteen baseline propositions aimed at reframing discourse on internet governance, providing a foundational framework for understanding and addressing the complexities of governing the internet effectively.

How safe are we? Security risks of the social networks
We are witnessing an extreme proliferation of the social networks, which can be seen in two ways: an expansion of social network websites, and an increase in the number of people who are starting to use them. The author describes the risks associated with social networks, mostly associated with user's privacy, and the responsibility for those risks. This paper also analyses whether the rules proscribed so that social network providers can distance themselves from possible abuses are really designed to help the users be safe.
The Hypocrisy Threatening the Future of the Internet
The message highlights the threat of hypocrisy to the future of the internet, raising concerns about the negative impact of inconsistent actions and standards on the digital landscape.

Opening one’s eyes to opportunity
'John Walubengo introduced me to KictaNET... I got involved in ICT and... what it could do at a time when Kenya was revising its national ICT policy...' - Judith Okite from Kenya

The impact of development on a society
‘A critical activity will be information dissemination – educating people about IG issues and assisting them in formulating views and opinions that can not only be applied to their lives, but which can be communicated to national and regional leaders as appropriate.’ - Michele Marius from Jamaica

Bridging the digital divide
‘Internet governance (IG) is a new field which lacks expertise in Madagascar. Some of the pressing issues in Madagascar are the digital divide, IT illiteracy, and the inadequacy of national jurisdiction with technology advances.’ - Zoniaina Fitahiana Rakotomalala from Madagascar
The EU’s New Commission: Digital Policy in the Limelight (Briefing Paper #13)
In this briefing paper, Dr Stephanie Borg Psaila analyses Ursula von der Leyen's new EU Commission's emphasis on digital policy for 2019–2024.

Statecraft and foreign policy: India, 1947–2023
Statecraft and Foreign Policy provides an in-depth understanding of India’s rise as an economic and political power and its role in addressing global challenges, from climate change to international trade, security, health and energy. It focuses on India’s statecraft and foreign policy from its independence in 1947 to current politics and policies in 2023 – 75 years later.

Internet governance and service provision in Zimbabwe
From an Internet governance perspective, multilingualism and security have been two of the cornerstone themes since its inception. The security theme addresses topics regarding the Domain Names System (DNS), Public Key Infrastructure (PKI), Internet attacks, security awareness, and policies and legal measures to ensure a safe and secure Internet experience. Security is a very diverse area where multiple topics should be tackled, and ignoring one or more topics while securing other areas would still jeopardise the safety of Internet users.

The role of knowledge in the cyber-age of globalisation
In his paper, Richard Falk reflects on the application of information technology on diplomacy, and discusses the challenge of converting information technology to ‘knowledge technology’, and subsequently to ‘wisdom technology’. Yet, the ‘crossroads in human experience’ brings many challenges and dangers which the author analyses.

Development Aid and Nigeria’s Poverty Challenge: Millenium Development Goals 4 and 5 in Focus
The quest to eradicate poverty has been identified as the most critical challenge facing development in the world today. Women and children are disproportionately affected by poverty.

Achieving Zero Hunger: The Critical Role of Investments in Social Protection and Agriculture
The message emphasizes the crucial role of investments in social protection and agriculture in achieving zero hunger.
Leaving No One Behind in the Data Revolution (Briefing Paper #5)
The text offers policy recommendations and insights on cybersecurity, focusing on building resilience, fostering cooperation, and addressing challenges in the digital domain.

Launching an ICT campus and beyond
'I found that living in a developed economy is quite different from living in my developing country environment. Things like the Internet are taken for granted...In sub-saharan Africa, lack of the same (Internet) resources would automatically discourage me...' - John Walubengo from Kenya
A Tipping Point for the Internet: Predictions for 2018 (Briefing Paper #9)
The briefing paper discusses various predictions for the internet in 2018, focusing on key trends and developments that will shape the digital landscape. Key areas include the rising importance of cybersecurity, the impact of artificial intelligence on online platforms, growing concerns over data privacy, increased regulation of tech giants, and the potential for blockchain technology to revolutionize various industries. These trends are expected to drive significant changes in how we use and interact with the internet in the coming year.

How effective is direct remote interaction in EuroDIG?
This report describes the evolution of remote participation in EuroDIG and provides an assessment of the current situation, focusing on the issue of inclusiveness by direct remote interaction. It also provides steps to improve and put in greater perspective the effectiveness and reach of remote participation hubs, as well as outlining further directions research can take regarding the networks of people and organisations mobilised in the process.

Electronic government equals sustainable development for Guyana
Electronic government (e-government) equals sustainable development for Guyana. This is the thesis illustrated by this paper along with the possible constraints involved in implementing e-government.

Making Education a Priority in the Post-2015 Development Agenda
The post-2015 development agenda should prioritize education to address global challenges effectively and promote sustainable development. Educational goals must encompass quality, inclusivity, equity, and lifelong learning opportunities for all individuals, regardless of background. Investing in education not only benefits individuals by improving their opportunities and well-being but also contributes to societal advancement by fostering economic growth, reducing poverty, and promoting social cohesion. Education is a fundamental human right and a key driver of progress, making it essential f...

The Internet and diplomats of the 20th century
The Internet and diplomats of the twenty century: how new information technologies affect the ordinary work of diplomats.
Reforms to the International Financial Architecture | Our Common Agenda Policy Brief 6
The international financial architecture is outdated and failing humanity. From egregious borrowing costs for developing countries to underinvestment in global crises like climate change and pandemics, the system is rife with inefficiencies and biases. It's a tale of two worlds, with a growing gap between the haves and have-nots, not just in wealth but in access to a secure future. The clock is ticking on ambitious reforms to make the world's financial architecture fit for the 21st century.

Le code du travail burkinabé face au télétravail: Comment adapter le code du travail burkinabé pour qu’il réponde aux exigences du travail à distance?
Les TICs et l’Internet particulièrement ont étouffé le fondement de la nécessaire présence physique du travailleur dans l’entreprise. Au Burkina Faso, ce contexte a créé de nouvelles opportunités dont le travail à distance, depuis l’accession du pays au cyberespace en 1996.

Tackling privacy issues
'It is necessary to focus the IGF discussion on the real problems associated with the collection and use of personal information. The reality is that there is very little that consumers can do today to protect their personal data...' - Katitza Rodriguez from Peru

Freedom of Expression on the Internet
The Internet for the first time entirely made possible the fulfillment of the Article 19 of the Universal Declaration "Everyone has the right to freedom of opinion and expression; this right includes freedom to hold opinions without interference and to seek, receive and impart information and ideas through any media and regardless of frontiers". On the Internet, everybody is, even unconsciously, sending or receiving information, sharing idea and changing views. However, at the same time it has again showed how diverse the world is and how cultural, political, religious and social differences m...
EspriTech de Genève
EspriTech de Genève, embodying the tech spirit of Geneva, focuses on responsible, human-centred AI that intertwines historical thought with modern governance and coding. Rooted in the city's rich thining and humanitarian heritage, it transforms classical values into practical AI applications. EspriTech de Genève is a technically and financially viable approach to AI transformation, moving from concept to actionable results in everyday technology use.

Updating International Geneva to the Data-driven Era (Briefing Paper #12)
In this briefing paper, Ms Rafaela Marinho and Mr Avi Krish Bedi outline their research on how international organisations (IOs) in Geneva address and use big data in their work.
Global Cross-Border Privacy Rules Declaration
The text discusses the need for trusted cross-border data flows to support economic growth and innovation. It introduces the establishment of a Global Forum to promote interoperability in data protection and privacy, aiming to enhance international cooperation and standards. The Forum is set to encourage the use of global systems, share best practices, and engage various stakeholders. Participation is open to jurisdictions accepting the Forum's principles, with decisions made by consensus. Regular meetings will determine activities and implementation, with the possibility of additional gatheri...

Emerging Leaders for a Digital World (2011): Dalsie Greenrose Kalna Baniala from Vanuatu
‘With the number of training courses I have attended, including attending the Internet Governance Forum (IGF), I have learnt a lot.’

Towards a secure cyberspace via regional co-operation
The study Towards a secure cyberspace via regional co-operation provides an overview of the international dialogue on establishing norms of state behaviour and confidence-building measures in cyberspace.

Policy and regulatory challenges to deploying blockchain technologies
Abstract: Blockchain technologies are heralded by some as one of the most promising innovations after the Internet. The concept’s origins are linked to Bitcoin, a paperless cryptocurrency, and the first decentralized digital currency that works without a central bank or single administrator.

Promoting e-Commerce in developing countries
This study examines the advantages and possibilities for the use of digital signatures to carry out electronic transactions. It focuses on developing and transition countries that have not fully implemented the use of digital signatures in their economic, commercial and productive processes. An important aim of this research is to create awareness on the likely effects for enforcing the use of digital signatures to carry out e-commerce transactions on the economies of developing and transition countries. The study also proposes key issues to be considered for policy-makers in countries in orde...

E-learning at Fiji National University
In this paper, Fiji National University (FNU) was used to determine the possibility of e-learning. A new programme was chosen and a programme document was written. Based on the programme, a unit syllabus was developed. Given the infrastructure of the information and communication technology (ICT) department at FNU, this project will be deployed as a pilot project for evaluation and monitoring of e-learning research.

Enyclopedia of International Development
The Encyclopedia of International Development is a comprehensive resource that covers a wide range of topics related to development, including theories, practices, actors, and key issues. It offers insights from various disciplines and perspectives, making it an invaluable tool for researchers, policymakers, and practitioners in the field of international development.

The need for IG regimes and representation
‘Indeed, the Internet can be a doubleedged sword. Consequently, given man’s innate quest to have stability, reliability, and certainty in his life, governance of the Internet is only a natural evolution.' - Valmikki Singh from Guyana

Developing awareness of IG issues
‘While employers and tertiary institutions have been providing Internet access to their employees for the last 10–12 years, the majority of Fijians have only been able to afford Internet access at home within the last five or six years...’ - Sam Goundar from Fiji

NETmundial Multistakeholder Statement
The NETmundial Multistakeholder Statement emphasizes the importance of a collaborative approach between stakeholders in addressing Internet governance issues. It highlights principles such as human rights, open standards, and transparent processes as key foundations for managing the Internet. The statement calls for shared responsibility, inclusivity, and diversity in decision-making processes to ensure a free, open, and secure cyberspace for all.

The Information Society Library
The Information Society Library (ISL) is a series of non-technical booklets providing information and guidelines on key cyberspace- and Internet-related issues.

How is trust defined in Internet governance organisations? (applied ethics in not-for-profit Internet organisations, managing critical Internet resources – a case study on trust)
The message addresses the definition of trust within Internet governance organizations, focusing on applied ethics in not-for-profit Internet entities managing critical Internet resources. Trust is a central component explored through a case study, examining the dynamics and importance of trust within these specialized organizations.

UNCTAD Digital Economy Report 2021
The Digital Economy report 2021 provides a review of studies dealing with cross-border data flows and analyses the inequalities in the data-driven digital economy. The Report looks at existing governance approaches at national, regional and multilateral levels, with a bearing on data flows. It calls for a balanced approach to global data governance that could help ensure that data can flow across borders as freely as necessary and possible, while achieving an equitable distribution of benefits, within and across countries; and addressing risks related to human rights and national security.

A New Diplomacy for Sustainable Development: The Challenge of Global Change
The text discusses the need for a new diplomacy approach to address the challenges of global change and foster sustainable development.

The World Summit on the Information Society (WSIS)
Written just before WSIS 2005, Petru Dumitriu takes us through an accounted journey of the WSIS process from 2003 in Geneva to the preparatory stages of the Tunis Summit in 2005. In this chapter Dumitriu also put forward suggestions for a post-multistakeholder summit where all stakeholders could use their creativity and resources to consolidate what has been established and to develop new forms of dialogue and partnership among themselves.

Sustainable Capacity Building: Internet Governance in Africa – An Action Plan
Enhancing sustainable capacity building on internet governance (IG) would have positive consequences within and beyond the African context. Considering the importance of the issues that fall under the framework of IG – ranging from providing access to infrastructure to promoting cybersecurity and fostering emerging technologies – it is possible to conclude that strengthening IG capacity building could ultimately contribute to developing the capacities required for implementing the Digital Transformation Strategy for Africa (2020-2030) (African Union, 2020a) and the Agenda 2063 (AU Commi...

Marrying education with ICT
‘It is necessary to ensure the responsible use of technology and to stress the innovation and knowledge sharing that technology allows over the opportunity for piracy, slander, and other ‘negative’ activities’ - Arlene Buckmire-Outram from Grenada

Australian aid: Promoting prosperity, reducing poverty, enhancing stability
The text is about Australian aid focusing on promoting prosperity, reducing poverty, and enhancing stability.

Crossing the Executive Digital Divide
Information and communications technologies (ICT) have become critical in business, government, manufacturing, critical infrastructures, academia, and, literally, everywhere else, and yet, despite the large sums of money involved, ICT remains the least well understood function in an organization.

Peacetime Regime for State Activities in Cyberspace
The publication covers in a multi-disciplinary approach the technical, legal, policy and diplomacy aspects of State activities in cyberspace during peacetime. It consists of 23 chapters of academic nature, elaborated by 24 authors specialised in the respective areas of expertise. Diplo's Dr Jovan Kurbalija contributed the chapter on E-diplomacy and Diplomatic Law in the Internet Era.

The benefits of e-learning
'There is a difference from taking a physical course, and some nuances of real-world, human interaction were missing. Yet, in a way, this difference helped me to concentrate better... in e-learning, one can stay more focused...' - Janyl Bokonbaeva from Kyrgyzstan

Glosario de Acrónimos de Gobernanza de Internet
La última edición del Glosario de Acrónimos de Gobernanza de Internet, compilado por DiploFoundation, contiene explicaciones de más de 130 acrónimos, inicialismos y abreviaturas utilizados en la jerga de la gobernanza de Internet. Además del término completo, la mayoría de las entradas incluyen una explicación concisa y un enlace para obtener más información.

Stakeholderism in African Internet Governance: the Case of the .africa gTLD
In 2012, ICANN announced plans to delegate over 1000 new generic top level domain names, one of which was the long awaited .africa.

For an effective taxation of electronic commerce in Madagascar
This research paper focuses on the taxation of electronic commerce (or e-commerce) in Madagascar. The objectives of this project are to offer insight and help the fiscal administration for future governmental programmes focusing on the taxation of e-commerce in Madagascar.

Exploring the need for speed in deploying information and communications technology for international development and bridging the digital divide
This paper comes on the eve of the millennium development goals deadline of 2015 which acknowledges ICT as the enabler for speeding towards the finish line. The quest is to explore whether we are all speeding towards a clearly defined goal, given our varied capacities and affinities.

Introducción a la Gobernanza de Internet
Aunque la gobernanza de Internet trata de los fundamentos del mundo digital, la gobernanza no puede manejarse con la lógica digital binaria de lo verdadero o lo falso, lo bueno o lo malo. En cambio, el sujeto exige muchas sutilezas y sombras de significado y percepción, requiriendo un enfoque analógico, cubriendo un continuo de opciones y compromisos. El objetivo del libro Introducción a la Gobernanza de Internet, del Dr Jovan Kurbalija, es proporcionar una visión general de los principales temas y actores en el campo a través de un marco práctico para el análisis, discusión, y resolu...

An Introduction to Internet Governance
'An Introduction to Internet Governance provides an excellent entry point. It has introduced many diplomats and officials to this emerging field of global policy. For others, it will stimulate reflections from linguistic, legal, and other perspectives. This book clearly shows that although the Internet is a ‘technical’ invention, its governance is far from simply a technical issue. Kurbalija’s book highlights the legal, social, linguistic, and economic perspectives of Internet governance. It is an impressive introduction to this emerging field of global policy' Nitin Desai, former Chai...

Breaks through the barriers of development
‘Capacity building is necessary to allow for equal participation... It will require all of us who have leadership positions to gain more knowledge to be able to provide, promote, and support Internet access for all.’ - Angelic Alihusain-del Castilho from Surinam
Statement on the Common Heritage of Mankind to the Internet’s critical infrastructure by Dr Alex Sceberras Trigona, Malta
Dr. Alex Sceberras Trigona raises questions about whether the Internet should be considered part of the Common Heritage of Mankind, emphasizing the need for international recognition and protection to ensure its proper management and safeguarding for current and future generations.

Evaluation du statut de l’E-Gouvernement en Union des Comores
L’e-gouvernement consiste à l’utilisation des Technologies de l’Information et de la Communication (TIC) par un gouvernement pour transformer sa façon d’administrer, de produire et de délivrer efficacement des services publics aux citoyens.

From a Safer Internet to a Better Internet for Kids
The text is about transitioning from a safer internet to a better internet for kids.

The waning of the state and the waxing of cyberworld
This paper discusses whether IT is functioning mainly as an instrument of states in their quest for power and wealth or is principally operating as a transformative agent by market forces and various sectors of civil society.

Report of the Intergovernmental Committee of Experts on Sustainable Development Financing
Report of the Intergovernmental Committee of Experts on Sustainable Development Financing.

Searching for Meaningful Human Control. The April 2018 Meeting on Lethal Autonomous Weapons Systems (Briefing Paper #10)
In this briefing paper, Ms Barbara Rosen Jacobson analyses the debate of the April 2018 meeting of the Group of Governmental Experts (GGE) of the Convention on Certain Conventional Weapons (CCW). The group was established to discuss emerging technologies in the area of lethal autonomous weapons systems (LAWS).

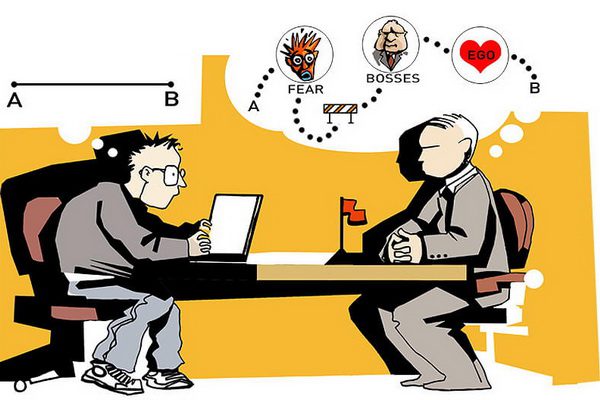
The secret life of a cyber vulnerability
The comic brings a worrying, yet realistic and educative story that follows a life of a cyber vulnerability, from its inception to its deployment for an actual cyberattack.

The Milennium Development Goals Report 2015
The Millennium Development Goals Report 2015 reflects on the progress made towards achieving the eight goals set by world leaders in 2000. It highlights significant accomplishments in areas such as poverty reduction, child mortality, and access to clean water. However, challenges remain, including disparities among regions and persistent inequalities. The report emphasizes the need for continued efforts to address these issues and accelerate progress towards sustainable development.

Transforming Our World: The 2030 Agenda for Sustainable Development
Transforming Our World: The 2030 Agenda for Sustainable Development is a comprehensive plan that outlines 17 goals aimed at ending poverty, protecting the planet, and ensuring prosperity for all. It addresses challenges such as climate change, inequality, and peace and justice. The agenda emphasizes the importance of partnerships, data, and financing in achieving these goals. Implementing the agenda requires a collective effort from governments, businesses, civil society, and individuals to create a more sustainable and equitable world by the year 2030.

A sustainable project with great results
It is a sustainable project with great results. The participants of our capacity building projects are currently taking charge of managing local initiatives, drafting regional ICT policy plans and training their own teams.' - Dhrupad Mathur from India

Digital Opportunities for All: Meeting the Challenge
The text is about embracing digital opportunities to overcome challenges and ensure access for all.

Making the link between IG and e-learning
‘Students and teachers do not have to sit in the classroom or be face-to-face but can now take part in e-learning from anywhere in the world and at any time, thanks to online facilities.’ - Shareeni Kala from Fiji

Facing challenges for developing countries
'Development challenges are enormous for Africa and they go beyond promoting information and communication technology. One important issue currently is how Africa will solve its energy problems, which are a threat to progress on the continent.' - Ken Lohento from Benin

Pricing the right to education: The cost of reaching new targets by 2030
This paper shows there is an annual nancing gap of US$39 billion over 2015-2030 for reaching universal pre-primary, primary and secondary education of good quality in low and lower middle income countries.

Facing the challenges of an Africa-wide ICT strategy
'There is a need to address these challenges to enhance the capacity of the AU organs, institutions and member states to better respond to instances of ICT policy in Africa. As part of the evolving African governance architecture, there is a need to formulate an ICT strategy...' - Eliot Nsega from Uganda

From Harmonising Cyberpolicies to Promoting Twiplomacy: How Diplomacy Can Strengthen Asia-Europe’s Digital Connectivity
This text was published in the ASEF Outlook Report 2016/2017.

Internet Governance Acronym Glossary
The 2019 edition of the Internet governance Acronym Glossary, compiled by DiploFoundation, contains explanations of over 150 acronyms, initialisms, and abbreviations used in IG parlance. In addition to the complete term, most entries include a concise explanation and a link for further information.
An International Digital Strategy for the European Union
The European Commission's Joint Communication outlines an International Digital Strategy aimed at enhancing the EU's global tech competitiveness and innovation. Acknowledging the digital and AI revolution, the EU emphasizes the need for collective action with international partners to ensure economic security and uphold democratic values. The strategy encompasses boosting tech capacity, establishing secure digital infrastructure, addressing cybersecurity threats, and promoting AI governance. By expanding partnerships and digital trade agreements, the EU aims to shape global digital governance ...
The Vulnerability of the Small Island Developing States of the Caribbean
The Small Island Developing States of the Caribbean are highly vulnerable to external economic and environmental shocks due to their small size and limited resources, which threaten their sustainability and development.

World Summit on the Information Society and development of Internet diplomacy
The purpose of this paper is to identify new developments and innovations in diplomatic practice resultant from the WSIS and WGIG. First, the author describes the overall WSIS framework and specific aspects of the WGIG. Second, he identifies the new developments and innovation in diplomatic practice that are likely of lasting importance. The author does so by comparing WSIS diplomatic practice to the practices developed during other major UN summits held since the Rio Earth Summit in 1992.

Decoding Disinformation: Lessons from Case Studies
The evolution of the internet over the years has played a crucial role in the access to and dissemination of information. The digitalisation of news portals, the creation of social media, and the presence of AI have not only contributed to informing people about everyday news but also allowed the fast spread of mis- and […]

Special Ministerial Event on Food Security and Sustainble Development in Small Island Developing States
A summary of the Special Ministerial Event on Food Security and Sustainable Development in Small Island Developing States.

Factors influencing broadband adoption and digital content consumption in developing countries: A case from Pakistan
This paper attempts to redress the issues of broadband adoption and digital content consumption and provides detailed analysis on the factors that influence them, and rejection determinants in a developing country like Pakistan.

Book of Abstracts (Internet Governance)
This collection of abstracts comes from from research projects conducted during the 2010/2011 Internet Governance Capacity Building Programme (IGCBP).

Measuring the Information Society Report 2015
The Measuring the Information Society Report 2015 provides insights into trends related to information and communication technologies globally.

Cybersecurity competence building trends
Report on cybersecurity competence building trends in OECD countries.

Defining development in the context of current realities
‘My personal knowledge reflects other cultures and types of people in Fiji and the Pacific. I live not only with one race but with many who have different cultural and traditional values.’ - Anju Mangal from Fiji

Work Programme on Electronic Commerce
The text outlines the World Trade Organization's work program on electronic commerce, focusing on discussions and negotiations aimed at establishing rules and frameworks to govern digital trade in the global economy.

Data protection on the Internet and its lack of regulation in Paraguay: adequate regulation for call centres
This research focuses on data protection regulations in Paraguay in order to analyse whether it contains provisions regulating the computerised processing of personal data and transborder data flows.
Understanding the Digital Divide
The digital divide refers to inequalities in access to and usage of technology. Factors such as income, education, geography, and age can contribute to this gap. Bridging this divide is crucial for ensuring equal opportunities for all individuals in today's technologically-driven world.

Education Counts: Towards the UN Development Goals
The text discusses the importance of education in achieving the UN Development Goals. It highlights the critical role education plays in economic growth, reducing poverty, improving health outcomes, and promoting gender equality. By investing in education, countries can address various societal challenges and work towards sustainable development.

The e-learning experience
'My vision for Malawi is to have educational institutions connected to the Internet and to each other. This would provide for reduction in cost, as we would... use lecturers/teachers from other institutions to teach students across the country...' - Ulemu Nyasulu from Malawi

Emerging Leaders for the Digital World
Emerging leaders, whose stories feature in this publication, are among 501 participants from 60 ACP countries who participated in the Capacity Development programme in ICT Policy and Internet Governance for Africa Caribbean and Pacific (ACP) 2010/2011.

The use of Information and Communications Technology (ICTs) in human rights promotion: A case study of the African Commission on Human and Peoples’ Rights
The employment of ICT tools as a weapon of choice at the African Commission on Human and Peoples' Rights, an organ established within the African Union with a broad mandate of spearheading human rights promotion on the African Continent has not been emphasised as a crucial element in the struggle towards achieving human rights promotion and protection on the African continent, with the resulting consequence that the Commission is not as visible and known to the people that it is supposed to serve.

The World Bank’s Contribution to Poverty Reduction in Peru
Peru’s economy has improved significantly, however poverty is an imperative issue that is not progressing as expected.

Oslo Summit: Financing Education in Developing Countries
The Oslo Summit focuses on financing education in developing countries to ensure access and quality education for all children.

Broadening the diplomatic bandwidth
‘I believe whistle-blowing websites have a greater role to play in the future of the humankind. These are a few of the issues that I became aware of through DiploFoundation, on whose blogosphere these issues continue to be debated.’ - Felix Samakande from Zimbabwe

Access of ICT benefits for underserved rural communities in developing countries: A case study from Nepal
Policy-makers and governments in developing nations can implement more effective policies and frameworks by gaining a better understanding of the factors that support stakeholders and partners to extend the benefits of information communication technology (ICT) to rural communities. The aim of this paper is to answer the framework to follow for extending access to ICT benefits in underserved rural areas of a developing country.

Emerging Leaders for the Digital World 2009
These pages contain the stories of talented people likely to play an important role in future Internet-related developments; all of them former participants in Diplo’s Internet Governance Capacity Building Programme (IG CBP) held between 2005 and 2007.

The network neutrality debate and development
This study focuses ont he Net Neutrality controversy. It aims to answer a number of questions including - If Net Neutrality deserves protection, the question is how? Should a political or legal solution be enacted at national or international levels? Can we trust an informal free-market solution that may develop on its own, or should legal and political means be used to enunciate this principle? Will market forces ensure the best outcome, whatever this may be?

The multistakeholder model in Internet policy-making: A case study of Paraguay
Internet Governance was a vague topic in Latin America and especially in Paraguay. Only after Snowden´s revelations of mass surveillance, the topic becomes familiar.

Intergovernmental organisations sharing and linking open and real-time data for inclusive governance
The rapid rise of the Internet has encouraged the use of open, real-time, and linked data to help understand and improve development processes.The advancement of data use for development without an Internet governance framework, however, raises the importance of inclusion of the most marginalized, as well as privacy and security. This paper will examine such issues, as well as the role inter-governmental organisations can play in helping to encourage the use of data while supporting the protection of privacy and security.

Small states in the global politics of development
Much of the discussion surrounding small states has treated them as a discrete category, with common vulnerabilities and opportunities. However, a productive approach is to look at the global politics of development, and then see where small states fit in. The author looks in turn at the global politics of finance, trade and the environment. He concludes that small states have been largely unsuccessful in asserting their own interests in global politics, and that (to the extent that it is possible to generalize about states which differ greatly) vulnerabilities rather than opportunities are th...

Internet governance (IG) as a diplomatic priority
This dissertation demonstrates that IG is a significant, emerging diplomatic process that should be studied and addressed seriously by diplomats to prepare them to manage the implications it has for future impact on global governance of the Internet.

Towards ‘concrete, physical, and local’
'This is not an outside imposition of technology, but an enthusiastic acceptance of support... the ideal situation, where just a push, just a bit of help, can enable the local population to maximise use of resources under their own direction.' - Virginia Paque from Wisconsin, USA

The Rise of TechPlomacy in the Bay area
Tech diplomacy is becoming a necessity for countries worldwide. Countries need to capture the nexus between technology innovation and economic developments. To be effectively present in the Bay Area, countries need to use innovative diplomatic approaches. This report discusses how tech diplomacy can be developed, and more specifically, how countries approach the Bay Area tech industry.

Internet Guide for Diplomats
The Internet Guide for Diplomats is the first guide specifically conceived and realised to assist diplomats and others involved in international affairs to use the Internet in their work. The book includes both basic technical information about the Internet and specific issues related to the use of the Internet in diplomacy. Examples and illustrations address many common questions including web-management for diplomatic services, knowledge management and distance learning.
EU Council conclusions on EU Digital Diplomacy
The EU Council emphasizes the urgent need for a coherent strategy in digital diplomacy amid geopolitical challenges, particularly following Russia's aggression against Ukraine. It calls for enhanced cooperation among EU Member States and global partners to uphold human rights, promote digital literacy, and foster a human-centric approach to technologies like AI. Key actions include addressing digital divides, bolstering resilience in Ukraine, and strengthening ties with Africa and other regions. The Council underlines the importance of collaboration with the tech sector and enhancing the EU’...

The use of ICT in human rights promotion: A case study of the African Commission on Human and Peoples’ Rights
The paper seeks to render a critical analysis that will lead and co-ordinate a programme of promotional work across the region, including the integration of ICT strategies in its promotional work.

Book of Abstracts – IGCBP Policy Research Project
Book of Abstracts – IGCBP Policy Research Project.
Interplay between Telecommunications and Face-to-Face Interactions: A Study Using Mobile Phone Data
The study explores the relationship between telecommunications and face-to-face interactions using mobile phone data.

Exploring the benefits of digital education
'The government of Nigeria is making a giant stride to improve the situation by rolling out programs that would in one form or the other include Information Technology in the curriculum of primary and secondary students.' - Ijeoma Ogbuagu from Nigeria

Development Effectiveness: What Have We Learnt?
The text discusses lessons learned regarding development effectiveness.

Improving the practice of cyber diplomacy: Training, tools, and other resources – Phase I
Cyber diplomacy, the conduct of diplomacy with respect to a state’s interests in cyberspace, is too important to ignore. Yet, the participation of countries is far from ideal.
DDoS – Available Weapon of Mass Disruption
The increasing militarisation of cyber-space comes in response to fears of critical damage caused by digital weapons like Distributed Denial-of-Service (DDoS). Understanding that the botnets are the key platform behind DDoS, we compared the costs of running a large-scale attack with the approximate downtime loss in a country-scale attack in case of Serbia, showing that DDoS are readily available weapons of possible mass disruption. Taken as a whole, this paper suggests responding to risks by combating cybercrime as the DDoS enabler, rather than by militarisation.

Diplomatic Reporting in the Internet Era
Paper delivered by Ambassador Victor Camilleri during the E-diplomacy panel on Diplomatic Reporting in the Internet Era after WikiLeaks, held on 9 February, 2011.

A developing country’s perspective on IG issues
'Among all the country members of the East African Community, only Burundi, my country, was absent from that EAIGF... That’s why, at the end of the IGF in Hyderabad, I came back with a new dream: An IGF Burundi.' - Jean Paul Nkurunziza from Burundi

Developing new ways to govern the Internet
'Even if I am participating in the process during the whole year and interacting with many people, meeting them face-to-face at an event like the IGF remains essential... it is the most effective way to network...' - Rafik Dammak from Tunisia

Unpacking Global Digital Compact: Actors, Issues, and Processes
Unpacking the Global Digital Compact explores the origins and impact of the Global Digital Compact (GDC), a new UN framework adopted at the 2024 Summit of the Future to shape digital and AI governance. This book explores the GDC's complex negotiations and its role in fostering global cooperation amid diverse perspectives and diplomatic challenges. Through accessible analysis and practical insights, it serves as a vital resource for understanding how the GDC aligns digital governance with the public interest and addresses the challenges of an increasingly complex policy landscape.

Bandwidth management: the public policy approach in a university campus network
This research presents an example of how evidence-based policy-making can lead to bandwidth optimisation in a university network, giving rise to improved network performance and cost savings.

The Feasibility of Information Communication Technology as a Tool for Development: Caribbean Community Perspectives
As a result of global trends relating to trade, many small economies continue to seek replacements for traditional markets which no longer offer preferential treatment.

Creating enabling environments for access to the Internet
'In most developing countries access to the Internet for people without disabilities is an issue. Thus the thought of access to people with disabilities is rarely considered.' - Emmanuel Edet from Nigeria

Information and communications technologies for development
The text discusses the role of information and communications technologies (ICTs) in development.

Digital Markets Act
The Digital Markets Act (DMA) aims to ensure the proper functioning of the EU internal market by 'promoting effective competition in digital markets' and, in particular, a fair and contestable online platform environment.
Data Diplomacy: Mapping the Field
The adoption of open data policies and the standardization of data collection were among the recommendations made during DiploFoundation's Data Diplomacy Roundtable: Mapping the Field, a brainstorming event that took place on 5 April 2017 – on the role of (big) data in international affairs and diplomacy.
The latest from Diplo and GIP
Tailor your subscription to your interests, from updates on the dynamic world of digital diplomacy to the latest trends in AI.
Subscribe to more Diplo and Geneva Internet Platform newsletters!
Diplo: Effective and inclusive diplomacy
Diplo is a non-profit foundation established by the governments of Malta and Switzerland. Diplo works to increase the role of small and developing states, and to improve global governance and international policy development.


