You may also be interested in

South Africa and the Simonstown Agreements
In John Young (ed.), The Foreign Policy of Churchill’s Peacetime Administration 1951-1955 (Leicester UP, 1988)

The Embassy: A story of war and diplomacy
This book tells the story of the vital role played by the US Embassy in Monrovia in helping to mediate an end to the brutal, 14-year civil war in Liberia in 2003.
DDoS – Available Weapon of Mass Disruption
The increasing militarisation of cyber-space comes in response to fears of critical damage caused by digital weapons like Distributed Denial-of-Service (DDoS). Understanding that the botnets are the key platform behind DDoS, we compared the costs of running a large-scale attack with the approximate downtime loss in a country-scale attack in case of Serbia, showing that DDoS are readily available weapons of possible mass disruption. Taken as a whole, this paper suggests responding to risks by combating cybercrime as the DDoS enabler, rather than by militarisation.

How important is the role of small states security in the maintenance of international peace and security?
The game of International Peace and Security has for a long time been one played only by the great powers, leading to the singling out of small states in its deliberations. These states would create their own rules and be their own referees, whilst the existing small states would conduct themselves as mere spectators. However, following the effects of the end of the two World Wars, the creation of the UN and decolonization, the role of small states in the maintenance of international peace and security has gathered new responsibilities and in consequence it has made them important agents and m...

Decision-Making in the UN Security Council: The case of Haiti, 1990-1997
Question: 'When is a "Foreword" not a "Foreword"? Answer: When it is written by Adam Roberts. This book started life as an Oxford doctoral thesis under the supervision of Professor Roberts, and the former supervisor has done both the former student and readers of this book a great service by prefacing it with a seven-page essay in which he underlines its importance in convincing detail. So this, unlike ninety-nine per cent of examples of the same genre, is a Foreword that should not be ignored.

Meeting the needs of microstate security
This article examines the pressing security concerns of microstates, particularly against the backdrop of recurring themes of vulnerability in the literature. It reviews those arguments in the early years of decolonization which expressed scepticism about the prospects for independence in such very small dependencies given their lack of defensive capacity and the geopolitical risks which they face in a potentially dangerous external milieu. The article argues that these doubts and concerns have not been realised in the actual experience of microstates particularly in terms of conventional thre...

DC Confidential: The controversial memoirs of Britain’s ambassador to the U.S. at the time of 9/11 and the Iraq War
DC Confidential: The controversial memoirs of Britain's ambassador to the U.S. at the time of 9/11 and the Iraq War.

Managing the Cold War: A view from the front line
Michael Alexander, a Russian-speaking senior British diplomat who died in 2002, was a major behind-the-scenes figure in what he calls the ‘management’ of the cold war to a peaceful conclusion.

DC Confidential: The controversial memoirs of Britain’s ambassador to the U.S. at the time of 9/11 and the Iraq War
The publication of these memoirs in autumn 2005 caused a public furore in Britain so I shall not waste time giving any background on Sir Christopher Meyer. (Just punch his name into Google, which will enable you in the blink of an eye even to find out from the BBC website which records he chose when he appeared on Desert Island Discs.)
The Clash of Civilizations
The Clash of Civilizations discusses the idea that cultural and religious differences will be the primary source of conflict in the post-Cold War world. The author argues that conflicts will arise along cultural fault lines, such as between Western and Islamic civilizations, rather than the political and economic divisions of the past. This perspective challenges the notion of a peaceful global community and emphasizes the importance of understanding and managing cultural differences to prevent future conflicts.

Cybersecurity in the Republic of Fiji
This paper discusses cybersecurity in Fiji and offers recommendations to challenges such as the vulnerability of systems due to lack of a cybersecurity framework. The poorly framed laws and lack of appropriate policies.

The Argentine seizure of the Malvinas [Falkland] Islands: History and Diplomacy
The Argentine seizure of the Malvinas [Falkland] Islands is a historical event that involves complex diplomatic implications.

War and the Private Investor: A Study in the Relations of International Politics and International Private Investment
The text is about the impact of war on private investors in the context of international politics and private investment.

Embassies under Siege
The article discusses recent attacks on embassies around the world, highlighting the increasing frequency of such incidents and the challenges faced by diplomats in maintaining security. Diplomatic missions have become targets for various groups due to political tensions and conflicts, putting staff and facilities at risk. Governments are working to enhance security measures and protect their embassies in response to these threats.

Small States and the Common Foreign and Security Policy (CFSP) of the EU: A Comparative Analysis
The text discusses the role of small states in the Common Foreign and Security Policy (CFSP) of the European Union, comparing their strategies and challenges.

Mediation in International Relations
The practice of mediation in international relations involves third-party intervention to facilitate conflict resolution between parties. Mediators act as neutral facilitators, assisting in communication, negotiation, and finding common ground to reach a peaceful resolution. It is a diplomatic tool used to de-escalate tensions, prevent conflicts, and promote cooperation among nations. Mediation often requires skilled mediators with expertise in conflict resolution and international affairs to navigate complex political dynamics and foster dialogue between conflicting parties.
Definition of Aggression | United Nations General Assembly Resolution 3314
The United Nations General Assembly Resolution 3314 (XXIX) establishes a Definition of Aggression for the purpose of maintaining international peace and security. It outlines acts that qualify as aggression, condemns war of aggression as a crime against international peace, and emphasizes that no justification can validate aggression. The resolution aims to deter potential aggressors, simplify identifying aggression, and protect the rights of victims.

A kind of diplomatic incantation: Exchanging British and Japanese diplomats in the Second World War
The content discusses how British and Japanese diplomats were exchanged during World War II in a diplomatic ritual that followed strict protocols to ensure the safety and respect of both parties.
Metaphor and War: The Metaphor System Used to Justify War in the Gulf
The text discusses how metaphors are used to justify war in the Gulf.

Diplomatic Security under a Comparative Lens – Or Not?
“Diplomatic security” is the term now usually preferred to “diplomatic protection” for the steps taken by states to safeguard the fabric of their diplomatic and consular missions, the lives of their diplomatic and consular officers, and the integrity of their communications; it has the advantage of avoiding confusion with the controversial legal doctrine of diplomatic protection.

Governance and conflict in the Mano River Union States: Sierra Leone a case study
The MRU states (Côte d’Ivoire, Guinea, Liberia and Sierra Leone) experienced more than two decades of bitter conflicts. With the exception of Guinea which was spared a full-scale civil war, the other three neighbouring MRU states went through violent civil conflicts which resulted in massive human suffering, social dislocation and the destruction of the region's economy.

The Role of Nigeria in Restoring Peace in West Africa
Remmy Nweke attempts a search into the rationale behind Nigeria‟s decision to make Africa the cornerstone of her foreign policy.

The Diplomatic Kidnappings: A Revolutionary Tactic of Urban Terrorism
The article discusses how diplomatic kidnappings have become a tactic of urban terrorism within revolutions, targeting diplomats to exert pressure on governments. Diplomats are seen as valuable assets by their home countries, making their abduction a powerful tool to achieve political objectives.

The National Security of Small States in a Changing World
The text discusses how small states must adapt their national security strategies to address the challenges presented by a rapidly changing global environment.

Embassies in Armed Conflict
Apologies for the oversight, please provide the content that you would like summarized.

The Role of Diplomacy in the Challenges to Maritime Security Cooperation in the Gulf of Guinea: Case Study of Nigeria
There is presently a pervading feeling that the West and Central African states are long overdue to take control of their maritime environment. However, these expectations show no indication of materialising in the short term.

Keeping the Peace in the Cyprus Crisis of 1963-64
After some difficulties, a UN force was established in Cyprus (UNFICYP) following the collapse of the bicommunal independence constitution of this former British colony - a constitution which the Greek Cypriots had always felt too favourable to the Turkish minority - at Christmas 1963. In this book, Alan James, Professor Emeritus of Keele University and leading authority on peacekeeping, provides what is likely to be regarded as the definitive history of the creation of this force.

The Fundamental Principles of the Red Cross: Commentary
The Fundamental Principles are the result of a century of experience. Proclaimed in Vienna in 1965, they bond together the National Red Cross and Red Crescent Societies, the International Committee of the Red Cross and the International Federation of Red Cross and Red Crescent Societies, and guarantee the continuity of the Movement and its humanitarian work. In this succinct commentary intended for the general public, Jean Pictet explains the meaning of each of the seven Fundamental Principles; he analyses them on the basis of different criteria and presents all their various aspects, thus mak...

Return to the UN: United Nations diplomacy in regional conflicts
‘… lively … persuasive … careful analysis… This is a very readable study, combining narrative strength with political acuity, and informative on the years of disappointment … Much has changed since the UN’s annus mirabilis, but Berridge’s conclusions still stand’, Nicholas Sims, London School of Economics, Millenium.

The Breaking of Nations: Order and Chaos in the Twenty-First Century
The message is a summary of the book "The Breaking of Nations: Order and Chaos in the Twenty-First Century.

Diplomats at War: British and Commonwealth diplomacy in wartime
In their Preface, the editors of Diplomats at War say that the two world wars in the twentieth century had a “catalytic impact upon the practice of diplomacy”; among other things, they continue, this produced “an unprecedented revolution” in the way heads of mission conducted their business.

Strengthening of the Coordination of Emergency Humanitarian Assistance of the United Nations
The text discusses the Strengthening of the Coordination of Emergency Humanitarian Assistance of the United Nations.

Conflict resolution and peace building (disseration by Unisa Sahid Kamara)
Unisa Kamara's dissertation seeks to give an account of the Sierra Leone conflict and the different measures and strategies including diplomatic attempts and efforts that were employed by various parties in trying to secure a peaceful and durable solution to it. The paper discusses the peace building measures and activities that were employed in sustaining the Sierra Leone peace process after the attainment of a negotiated settlement.

Spies in Uniform: British Military and Naval Intelligence on the Eve of the First World War
Matthew Seligman, who is a Senior Lecturer in History at the University of Northampton, sets as his target the claim - recently revived by Niall Ferguson - that the British decision for war in August 1914 was made despite the absence of any compelling evidence that Germany was prompted by a 'Napoleonic' design.

Modern Diplomacy – Opening address
Opening address of the Honourable Dr. George F. Vella, Deputy Prime Minister and Minister of Foreign Affairs and the Environment of Malta.

The Yugoslav diplomatic service under sanctions
Sanctions adversely affect all the structures of the state and society, and render difficult, if not impossible, the normal operation of services, including the Foreign Service.This paper discusses the challenges faced by the Yugoslav diplomatic service when the country was under sanction.

Diplomacy under a Foreign Flag: When nations break relations
The text is about diplomatic relations between countries and the implications of breaking these ties.

Peace Negotiations and Time: Deadline Diplomacy in Territorial Disputes
The text discusses the importance of time in peace negotiations for territorial disputes, emphasizing how deadlines can impact diplomacy and the need for effective time management in reaching agreements.

United Nations, Divided World, 2nd ed
The message is a placeholder and does not contain any actual content to summarize.

Peacetime Regime for State Activities in Cyberspace
The publication covers in a multi-disciplinary approach the technical, legal, policy and diplomacy aspects of State activities in cyberspace during peacetime. It consists of 23 chapters of academic nature, elaborated by 24 authors specialised in the respective areas of expertise. Diplo's Dr Jovan Kurbalija contributed the chapter on E-diplomacy and Diplomatic Law in the Internet Era.

Diplomacy Before and After Conflict
The importance of diplomacy in preventing conflicts is highlighted in this text. Diplomatic efforts both before and after conflicts are crucial for resolving disputes peacefully. Diplomacy plays a key role in preventing escalation of tensions, promoting understanding, and finding mutually acceptable solutions. It emphasizes the need for respectful communication, negotiation, and compromise to maintain peace and stability in the international arena. Diplomatic channels must be utilized effectively to address grievances, build trust, and foster cooperation among nations. Diplomacy is a vital too...

A Declaration of the Independence of Cyberspace
A declaration of independence for cyberspace, asserting that traditional governments have no authority over this virtual realm. Barlow believes that cyberspace should be free from external regulation and should be governed by the individuals who inhabit it.

All Fall Down: America’s fateful encounter with Iran
All Fall Down is the definitive chronicle of Americas experience with the Iranian revolution and the hostage crisis of 1978-81. Drawing on internal government documents, it recounts the controversies, decisions and uncertainties that made this a unique chapter in modern American history. From his personal experiences, the author draws revealing portraits of the people who engaged in this test of wills with an Islamic revolutionary regime.

Dealing with cybersecurity challenges
'Various governments have come up with different interventions to address these challenges, like cybersecurity which is on the rise. The development of human resource and capacity building has been identified as one of the stumbling blocks.' - Godfrey Ahuma from Ghana

Weapons Overview
The Weapons Overview provides an in-depth analysis of various weapons, including firearms, melee weapons, and explosives, covering their specifications, advantages, and best use scenarios. It aims to assist readers in making informed decisions regarding weapon selection for different situations.
The Falkland Islands War: Diplomatic Failure in April 1982
The text discusses how the Falkland Islands War of April 1982 was a diplomatic failure.

The Search for Peace
The text discusses the importance of seeking peace within oneself and in the world around us. It emphasizes the impact of personal inner peace on creating a harmonious environment globally. The text suggests that by finding peace within ourselves, we can contribute to fostering peace on a larger scale.

Internet governance and service provision in Zimbabwe
From an Internet governance perspective, multilingualism and security have been two of the cornerstone themes since its inception. The security theme addresses topics regarding the Domain Names System (DNS), Public Key Infrastructure (PKI), Internet attacks, security awareness, and policies and legal measures to ensure a safe and secure Internet experience. Security is a very diverse area where multiple topics should be tackled, and ignoring one or more topics while securing other areas would still jeopardise the safety of Internet users.

High Noon in Southern Africa: Making Peace in a Rough Neighbourhood
The text is about the challenges of achieving peace in Southern Africa amid regional conflicts and political instability.

Introducing child safety in Romanian schools: Does the existing primary and secondary curriculum address online safety?
This paper examines the idea of an online child safety policy for Romania, which would provide an initiative to encourage smart online behavior in young children, prepare them to surf the Internet, and educate them to avoid its dangers. As technology develops and more and more children spend time online, they are exposed to numerous threats, dangers and potential abuse. Children need to learn how to behave online, how to critically assess their activities online and act accordingly.

Female leadership in conflict prevention, diplomacy and UN peacekeeping initiatives
The importance of female leadership in conflict prevention, diplomacy, and UN peacekeeping initiatives is highlighted in the following text.

International Politics: States, Power and Conflict since 1945, Third Edition
This textbook is designed to support a general undergraduate course on International Relations. It is based on the second year course which I taught at the University of Leicester in the late 1970s and 1980s. The book was first published in 1987 and was brought out in a second, fully revised edition in 1992. The third edition was published by Prentice-Hall/Harvester Wheatsheaf in paperback in 1997 and is now available in a Pearson Education ‘Print on Demand’ edition (ISBN 0-13-230327-2).

Lethal Autonomous Weapons Systems: Mapping the GGE Debate (Briefing Paper #8)
The paper discusses the ongoing debate in the Group of Governmental Experts (GGE) on Lethal Autonomous Weapons Systems (LAWS) and the varying perspectives on the need for regulation and control of these weapons.

South Africa
In R. Allison and P. Williams (eds), Superpower Competition and Crisis Prevention in the Third World (Cambridge UP, 1989), pp. 206-16.

Preventive Diplomacy: Stopping Wars Before they Start
The text discusses the concept of preventive diplomacy as a proactive approach to preventing wars before they begin.

International multistakeholder cyber threat information sharing regimes: Policy considerations for scaling trust and active participation
This paper examines cybersecurity information sharing mechanisms. It looks at the research into public-private partnership (PPP) theory, their application for cybersecurity, and the burgeoning field of international cybersecurity collaboration, and draws conclusions on what policy elements are needed to foster success in architecting a platform for cybersecurity information sharing on a large scale. The paper surveys existing information sharing regimes and the policy objectives they attempt to reach, including capacity building, standardized languages for information sharing, liability prote...
From U Thant to Kofi Annan: UN Peacemaking in Cyprus, 1964-2004
2004 marked the fortieth anniversary of the United Nations presence in Cyprus. Since March 1964, the UN has been responsible for addressing and managing both peacekeeping and peacemaking efforts on the island.

Post Cold War diplomatic training
Victor Shale's paper refers to a specific time period: the post-Cold War period which brought about new forms of conflicts, and high levels of terrorism. In the light of the change in traditional diplomacy, his paper examines multistakeholder diplomatic training and its importance as an approach in penetrating different cultures, and examines whether this approach could be used to minimise intractable conflicts.

The Peace Brokers: Mediators in the Arab-Israeli Conflict, 1948-79
The text discusses the role of mediators in the Arab-Israeli conflict from 1948 to 1979.

John le Carré: The Biography
I thought to review this book because I had enjoyed the spy novels of John le Carré and, having introduced a chapter on secret intelligence into the latest edition of my textbook and mentioned him in it (p. 155), was keen to see if Adam Sisman had turned up anything new about the novelist’s own short career as an intelligence officer in what was then West Germany.

Virtual Reality and the Future of Peacemaking (Briefing Paper #14)
The briefing paper discusses the potential of virtual reality in fostering peacebuilding efforts worldwide. Through VR technology, individuals can develop empathy, understand different perspectives, and communicate effectively, facilitating conflict resolution. VR applications can simulate real-life scenarios, promote dialogue, and reduce prejudice by experiencing situations from another's point of view. This innovative approach has the potential to enhance peacebuilding initiatives and create a more connected and understanding global community.

Mediation in the Yugoslav Wars: The Critical Years, 1990-95
The book "Mediation in the Yugoslav Wars: The Critical Years, 1990-95" explores the role of mediation in the Yugoslav Wars during the crucial period from 1990 to 1995. It delves into the efforts made by various individuals and organizations to mediate the conflicts that arose during this time. Through a detailed examination of mediation attempts, the book sheds light on the complexities and challenges faced in trying to bring about peace in the region.

The secret life of a cyber vulnerability
The comic brings a worrying, yet realistic and educative story that follows a life of a cyber vulnerability, from its inception to its deployment for an actual cyberattack.

Education and Conflict: Complexity and Chaos
The relationship between education and conflict is intricate and tumultuous. Factors such as historical influence, societal norms, and educational policies all contribute to this complex dynamic. Conflicts can disrupt education systems and vice versa, leading to a chaotic environment where the role of education in promoting peace and reconciliation becomes crucial. Understanding this complexity is essential for addressing conflicts and creating sustainable peace-building efforts.

Culture and Conflict: Challenges for Europe’s Foreign Policy
The text discusses the challenges that Europe's foreign policy faces due to cultural differences and conflicts.
Intractable Syria? Insights from the Scholarly Literature on the Failure of Mediation
The article discusses the challenges and reasons behind the failure of mediation efforts in Syria based on scholarly literature.

The Mediation Process: Practical Strategies for Resolving Conflict
The Mediation Process: Practical Strategies for Resolving Conflict offers guidance on effectively resolving conflicts through mediation.

Managing Global Chaos
The message deals with strategies for managing global chaos. It discusses the importance of adaptability, resilience, and communication in navigating turbulent international waters. Leaders are advised to anticipate challenges, foster collaboration, and maintain a proactive approach to addressing crises on a global scale. The text emphasizes the need for flexibility and innovation to effectively manage chaos in a rapidly changing world.
Track 2 diplomacy and Pakistan
Track 2 diplomacy refers to unofficial interactions involving non-governmental actors to facilitate communication and conflict resolution. In the context of Pakistan, such diplomacy can help bridge gaps between governments, promote understanding, and contribute to peaceful resolutions of issues.

An Examination of the Role of Women in Conflict Management: Sierra Leone Case Study
This paper examines the role of women in conflict management, using Sierra Leone as a case study.

The development of multilateral diplomacy and its fundamental role in global security and progression.
This dissertation is written to present the notion of peace and security to be the direct result of international cooperation through multilateral means

The Revenge of Geography: What the Map Tells Us About Coming Conflicts and the Battle Against Fate
The Revenge of Geography discusses how the physical and political landscapes influence global conflicts and shape our destinies.
Diplomatic security and the birth of the compound system
The text discusses the importance of diplomatic security and the development of the compound system to enhance safety measures for diplomatic missions.

Exploring the Relevance of Engagement and Containment Approaches in the European Union’s Management of Relations with Russia
Since 2006, Russia has grown more assertive and even hawkish in its approach to the European Union (EU), even seen as attempting to divide the large EU membership so as to consolidate its influence in Europe.

A New Generation Draws the Line: Kosovo, East Timor and the Standards of the West
Note: The author of this review compares Noam Chomsky's A New Generation Draws the Line: Kosovo, East Timor and the Standards of the West and David Fromkin's Kosovo Crossing: American Ideals meet Reality on the Balkan Battlefields.

International domain names from a multilingualism and security perspective
From an Internet governance perspective, multilingualism and security have been two of the cornerstone themes since its inception. The security theme addresses topics regarding the Domain Names System (DNS), Public Key Infrastructure (PKI), Internet attacks, security awareness, and policies and legal measures to ensure a safe and secure Internet experience. Security is a very diverse area where multiple topics should be tackled, and ignoring one or more topics while securing other areas would still jeopardise the safety of Internet users.

FDR’s Ambassadors and the Diplomacy of Crisis: From the rise of Hitler to the end of World War II
What effect did personality and circumstance have on US foreign policy during World War II? This incisive account of US envoys residing in the major belligerent countries – Japan, Germany, Italy, China, France, Great Britain, USSR – highlights the fascinating role played by such diplomats as Joseph Grew, William Dodd, William Bullitt, Joseph Kennedy and W. Averell Harriman. Between Hitler's 1933 ascent to power and the 1945 bombing of Nagasaki, US ambassadors sculpted formal policy – occasionally deliberately, other times inadvertently – giving shape and meaning not always intended by ...

Effectiveness of U.S. Economic Sanctions with Respect to Sudan
The U.S. economic sanctions on Sudan have had limited success in achieving their intended goals due to various factors. The sanctions have impacted the Sudanese economy and government, but they have also inadvertently harmed civilians and hindered humanitarian efforts in the region. Additionally, the sanctions have not been successful in promoting political change or addressing human rights violations in Sudan. The effectiveness of these sanctions remains a topic of debate among policymakers and analysts.

A New Wave for the Reform of the Security Council of the United Nations: Great Expectations but Little Results
The reform of the Security Council of the United Nations (UNSC) has been an elusive issue at the United Nations (UN). While practically all Member States agree on the need to change the structure of the most powerful body of the world organization, so far there has been no agreement about what elements of that reform or about the substance of the reform itself.

Cybersecurity in the Western Balkans: Policy gaps and cooperation opportunities
Report on cybersecurity cooperation in the Western Balkans.

Surrender is Not an Option: Defending America at the United Nations and Abroad
In the book "Surrender is Not an Option: Defending America at the United Nations and Abroad," the author emphasizes the importance of standing firm in defense of America's interests, explaining that surrender should never be considered as a viable option in international relations. The book likely offers insights into strategies for navigating diplomatic challenges while maintaining a strong stance on key issues.

Cybersecurity competence building trends
Report on cybersecurity competence building trends in OECD countries.

Health, security and foreign policy
Over the past decade, health has become an increasingly important international issue and one which has engaged the attention of the foreign and security policy community. This article examines the emerging relationship between foreign and security policy, and global public health. It argues that the agenda has been dominated by two issues – the spread of selected infectious diseases (including HIV/AIDS) and bio-terror. It argues that this is a narrow framing of the agenda which could be broadened to include a wider range of issues. We offer two examples: health and internal instability,...

Diplomatic Interference and the Law
Q: ‘Why will there never be a coup d’état in Washington? A: Because there’s no American Embassy there.’ This old joke serves to highlight the belief – entrenched deeply in poor, weak states – that diplomatic missions too often meddle in the ‘internal’ or ‘domestic’ affairs of the countries in which they are located, sometimes with dramatic consequences. It is a view that was held in the years following the Second World War by the former Yugoslavia, then struggling to extricate itself from the Soviet orbit, and prompted it to press successfully for the codification of dipl...

Kosovo Crossing: American Ideals meet Reality on the Balkan Battlefields
The author of this review compares Noam Chomsky's A New Generation Draws the Line: Kosovo, East Timor and the Standards of the West and David Fromkin's Kosovo Crossing: American Ideals meet Reality on the Balkan Battlefields.

The Demilitarization of American Diplomacy: Two cheers for striped pants
The trenchant contribution to this subject of the outstanding American scholar-diplomat Laurence Pope is published in Palgrave’s ‘Pivot’ series of short books designed to be brought out quickly.
The security of small nations: Challenges and defences
The 'essentially contested concept' of security is analysed, and some main kinds of ambiguity and dimensions outlined: level, kind of threat and kind of defence. Discourses on security, particularly of small nations, must avoid being trapped into dealing only with one level (national, which in practice normally means state), one kind of threat (military) and one kind of defence (again military). There is no clear relation between kind of alignment and military expenditures, but non-aligned states are overrepresented both among the very high armers and among the very low armers. Increasing gaps...

Regional water cooperation in the Arab – Israeli Conflict: A case study of the West Bank
The conflict between Israel and Arab countries, with several devastating wars, is about territory and land, and maybe just as crucially on the water that flows through that land. This dissertation, an analysis of the management of water in the West Bank, as a case study, seeks to underline the possibility of using soft power diplomacy, in addition to mediation and water cooperation, for a more collaborative kind of approach to the conflict.

Intervening in Africa: Superpower Peacemaking in a Troubled Continent
The text discusses superpower intervention in Africa for peacekeeping purposes.

Embassies as Command Posts in Anti-Terror Campaign
The use of embassies as command posts in the fight against terrorism is crucial for coordinating efforts and sharing intelligence across borders. Ambassadors play a key role in gathering and disseminating information to help prevent and counter terrorist attacks. This strategy enhances international collaboration, strengthens security measures, and improves the effectiveness of counterterrorism initiatives. By utilizing embassies as command posts, countries can work together more efficiently to combat the global threat of terrorism.

How safe are we? Security risks of the social networks
We are witnessing an extreme proliferation of the social networks, which can be seen in two ways: an expansion of social network websites, and an increase in the number of people who are starting to use them. The author describes the risks associated with social networks, mostly associated with user's privacy, and the responsibility for those risks. This paper also analyses whether the rules proscribed so that social network providers can distance themselves from possible abuses are really designed to help the users be safe.

Blundering Into Disaster: Surviving the First Century of the Nuclear Age
Blundering Into Disaster: Surviving the First Century of the Nuclear Age" discusses the history of nuclear weapons, their impact on global politics, and the potential threats they pose to humanity. The book explores past nuclear incidents and the dangers of accidental nuclear conflict, emphasizing the need for responsible decision-making to prevent catastrophic outcomes.

Tested in Times of Transition
The message focuses on navigating challenges during periods of change.

Barriers to conflict resolution in Africa: Mediating beyond power and ethnicity in the EAC and SADC countries through a Kenyan case study
This paper assesses the relevance of ethnicity and power in conflicts occurring in the EAC and SADC regions through a case study of Kenya. It engages with elites’ power contestation and the manner in which power has historically caused violence and instability in Kenya. Further, an account of researches on ethnicity and its inducing of violence is made. Through this, one discovers the importance of ethnicity beyond that of being a channel for the upsurge of violence.
The Responsibility to Protect
The Responsibility to Protect doctrine asserts that states have the responsibility to protect their populations from genocide, war crimes, ethnic cleansing, and crimes against humanity. When a state fails to do so, the international community must intervene responsibly to prevent and protect populations from mass atrocities. This principle emphasizes the importance of upholding human rights and promoting peace and security globally.

Searching for Meaningful Human Control. The April 2018 Meeting on Lethal Autonomous Weapons Systems (Briefing Paper #10)
In this briefing paper, Ms Barbara Rosen Jacobson analyses the debate of the April 2018 meeting of the Group of Governmental Experts (GGE) of the Convention on Certain Conventional Weapons (CCW). The group was established to discuss emerging technologies in the area of lethal autonomous weapons systems (LAWS).

Cyprus: the search for a solution
Lord Hannay, a senior British diplomat with great experience of multilateral diplomacy, retired in 1995 but was then persuaded to accept the position of Britain’s Special Representative for Cyprus. In this role he played an influential part in the UN-led effort to broker a settlement to the Cyprus conflict until the negotiations temporarily foundered in May 2003, when, with a mixture of relief and regret, he stepped down. (There is a postscript on the referendums held on the island in 2004 on the fifth version of Kofi Annan’s settlement plan.) He has written a brilliant account of the cour...

Against All Enemies: Inside America’s War on Terror
All memoirs are incomplete; instant ones even more so; and memoirs about security matters are the worst, in this respect. The book, however, manages to disappoint in an unusual way.
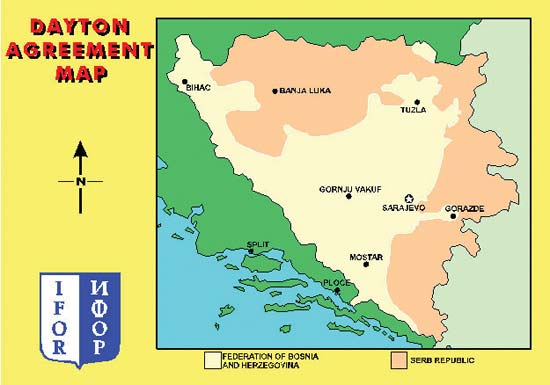
The Secret History of Dayton: U.S. Diplomacy and the Bosnia Peace Process 1995
The Secret History of Dayton: U.S. Diplomacy and the Bosnia Peace Process 1995 recounts the behind-the-scenes negotiations and strategies employed by American diplomats during the Dayton Peace Accords that ended the Bosnian War. The U.S. played a crucial role in brokering peace between the warring factions and outlining the terms of the agreement that led to the successful resolution of the conflict.

Lilliput under threat: The security problems of small island and enclave developing states
The article discusses the security challenges faced by small island and enclave developing states like Lilliput.
The latest from Diplo and GIP
Tailor your subscription to your interests, from updates on the dynamic world of digital diplomacy to the latest trends in AI.
Subscribe to more Diplo and Geneva Internet Platform newsletters!
Diplo: Effective and inclusive diplomacy
Diplo is a non-profit foundation established by the governments of Malta and Switzerland. Diplo works to increase the role of small and developing states, and to improve global governance and international policy development.


